We’ve been using passwords to identify ourselves on websites since the start of the internet, and we all have been told that our password should be secure but, do you know how attackers crack your password? The answer is password leaks. Now and then popular websites like LinkedIn and Facebook get their databases attacked and the passwords for millions of users get leaked to the internet, all of them are hashed passwords (a string of seemingly random characters).
When you register on a website hopefully they are storing your password making use of something called a hashing algorithm that takes your plain text password like “MyleakedPassword123” and turns it into a hash like “@6a8Agqu&EX&v$Lho*nXCYWua5YKo” attackers can take these hashes and use parallel processing hardware (like dedicated graphics cards) find out what the real password looks like:

By trial and error, the attackers try characters combinations and compare their hashes to the leaked hashes until they find a match.
How does this work?
There are two common types of attacks when trying to crack a bunch of password hashes, brute force, and dictionary attacks. Brute force attacks work by trial and error, a high-end GPU can handle about 40 billion tries per second depending on which hashing algorithm was used to encrypt the password.
A seven-digit long password consisting of lower case letters and 2 numbers is going to take seconds to crack just because of the amount of entropy the password holds. Password entropy is a measurement of how unpredictable, and therefore un-guessable the password is. A simple equation to find out all the possible combinations of strings using the characters you’re using for your password is:

Where C is the number of characters in your character set and L is the length of your password.
So for a password that would be 8 characters long that consists of 6 lower case letters and 2 numbers the calculation would be:
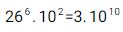
There are 26 letters in the alphabet and we power that to the amount of letters we are using in our password, the same applies to the two numbers we are using. That’s not a good number taking into account the number of tries per second a GPU is capable of.
The limitations of brute force attacks
Brute force attacks can be avoided by using longer passwords, which means they have way more entropy. But here’s where dictionary attacks come into play, dictionary attacks use a set of common keywords and real user passwords as a database of options to manipulate by using rules, a rule is a way of manipulating data.
A good example of a rule is to switch the letter “e” inside a word for a 3 or switch the letter “O” with a zero. You might think you’re clever by doing that but since everybody thinks the same it becomes predictable so attackers use that way of thinking against yourself. This type of attack it's especially effective when the right dictionary and the right rules are being used and it can be able to crack passwords up to 16 characters long easily if they follow common practices.
So, how should you choose a password?
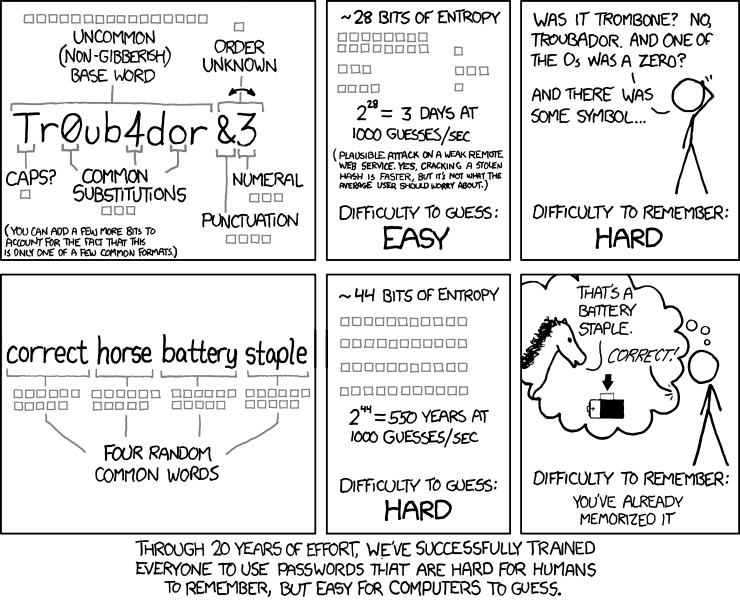
The comic above explains a way of choosing passwords that are easy to remember for humans and hard for computers to crack (as computers get faster it's easier for them to handle more complex passwords). Although it's not the best solution, you should be using 6 words and they should not be common words. The way of choosing these words should be random and should not depend on you, also you should take into account the pool of words you’re gonna choose from. A good rule might be to choose 6 random words from a list of 10,000 English words, and if you want to go deeper try mixing it up with some made-up words, switching different languages, and adding symbols in really random places.
Just use a password manager
Generally, passwords are not the best way of authenticating users and you should use multi-factor authentication as much as you can but passwords are going to stay with us for a long time. Ideally, you should be using a password manager, which acts as a vault for all your passwords so you only have to remember the master password that gives you access to your vault and it's your job to make sure that your master password is bulletproof. The good thing about using a password manager is that you can generate long random passwords whenever you want and store them so you don’t need to remember your passwords for all your different websites, you just need to remember your master password to access all your random passwords.
If you wanna check more resources about this topic I created a website a while ago with some videos that go more into detail: